
Social engineering manipulates or deceives employees to gain system access using tactics like phishing, spear phishing, and CEO fraud. Understanding these risks and providing targeted training helps strengthen your security posture.
Services
- Custom phishing campaigns to identify phish-prone users
- Targeted security awareness training
- Tailored phishing, vishing, and CEO Fraud simulations
- Detailed campaign reports
- Compliance-focused security awareness emails (HIPAA, CCPA, GDPR)

Phishing
- Phishing uses fake emails to steal sensitive data like passwords or credit cards.
- Common lures include fake CDC alerts, remote work scams, or Netflix messages, often via phishing kits imitating Google or Microsoft services.
Phishing Techniques
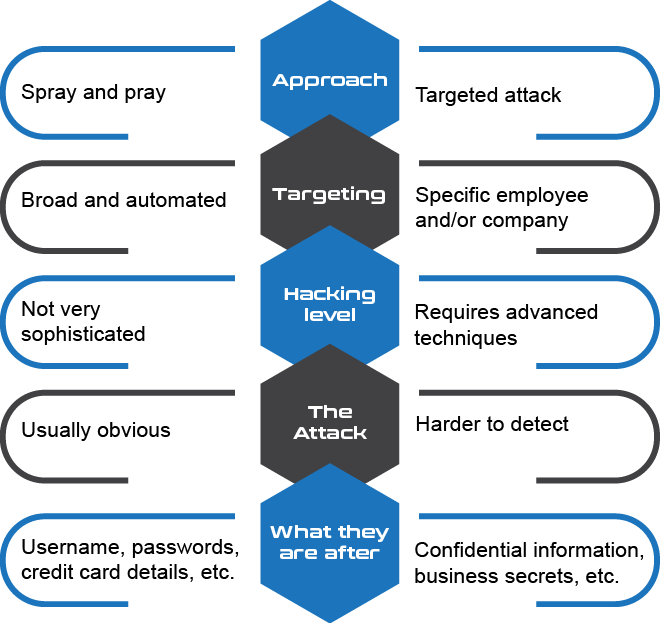
Spear phishing is an email targeted at a specific individual or department within an
organization that appears to be from a trusted source. It's actually cybercriminals
attempting to steal confidential information.
The same email is sent to millions of users with a request to fill in personal details.
These details will be used by the phishers for their illegal activities. Most of the
messages have an urgent note which requires the user to enter credentials to update
account information, change details, or verify accounts.
- Vishing is the phone's version of email phishing and uses automated voice messages to steal confidential information.
- These attacks try to trick an employee into giving out confidential information via a phone call.
- Vishing attacks use a spoofed caller ID, which can make the attack look like it comes from either a known number or perhaps an 800-number that might cause the employee to pick up the phone.
- Vishing often uses VoIP technology to make the calls.
- Vishing attacks can be focused on all employees, or against employees that mainly deal with people outside the organization. Departments like the help desk, PR, Sales, and HR are good to include in vishing security tests.
Phishing conducted via Short Message Service (SMS), a telephone-based text
messaging service. A smishing text, for example, attempts to entice a victim
into revealing personal information via a link that leads to a phishing website.
Phishing vs Spear Phishing

HIPAA Rules Regarding Text Messaging
- Access Control: Define who can text PHI.
- Audit & Reporting: Track and log message activity.
- Integrity: Prevent unauthorized changes or deletion.
- Authentication: Verify user identity.
- Transmission Security: Protect PHI from unauthorized access.


ecfirst Advanced Social Engineering Engagement
- AI-driven phishing emails and monthly social engineering exercises
- Targeted landing pages and failure training for users who fall for phishing.
- Up to 2 advanced training modules per failed user with automated enrollment and reminders
- Track user interactions: Opens, clicks, and data entry
- Monthly reports on failures, training progress, and industry comparison


