External Assessment
- Al-assisted open-source intelligence gathering
- DNS misconfiguration review
- Publicly leaked credentials search
- Anonymous extemal vulnerability scanning
- Website security testing (OWASP Top 10)
Wireless Assessment
- Facility walkthrough for rogue wireless networks
- Wireless security settings & Pre-Shared Key strength analysis
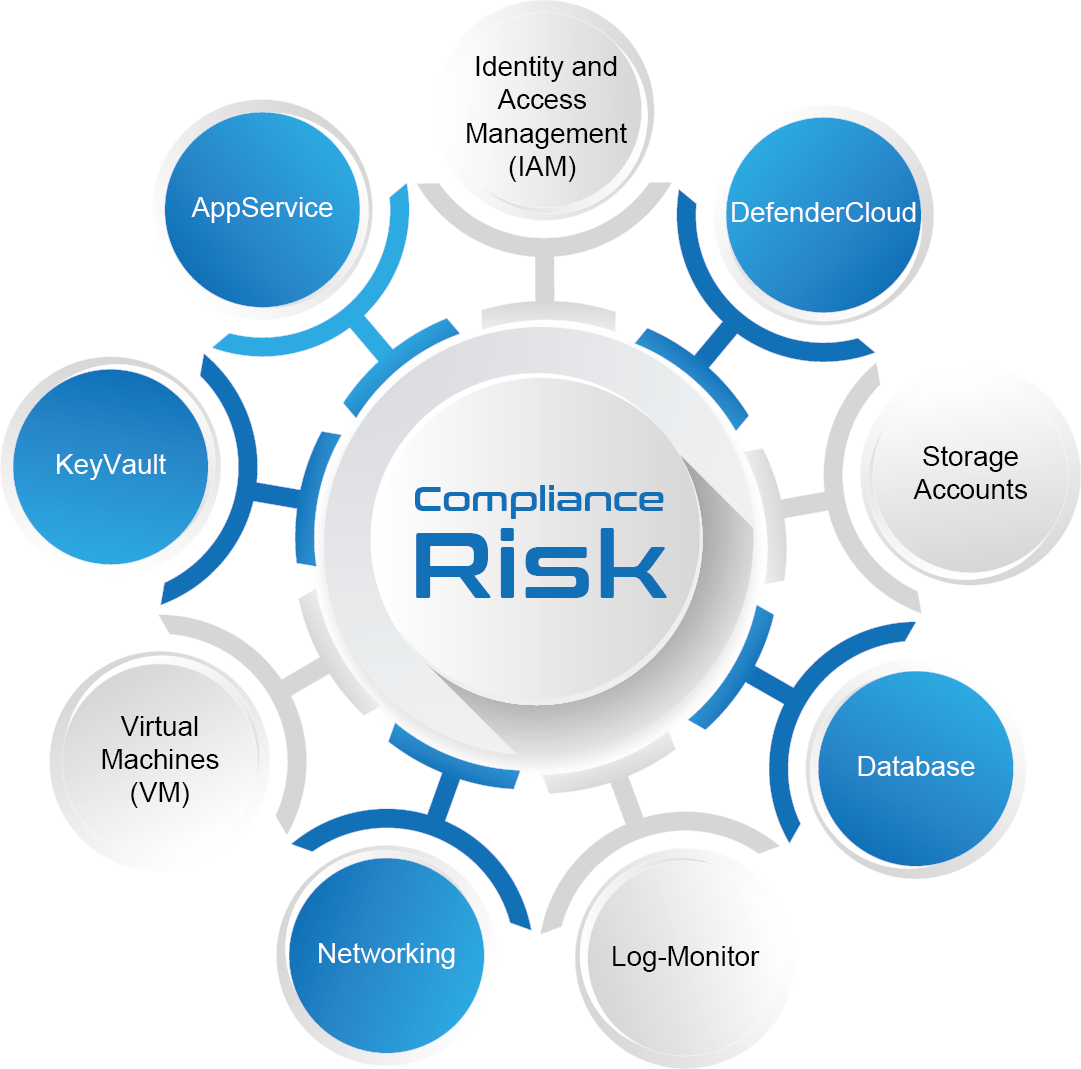
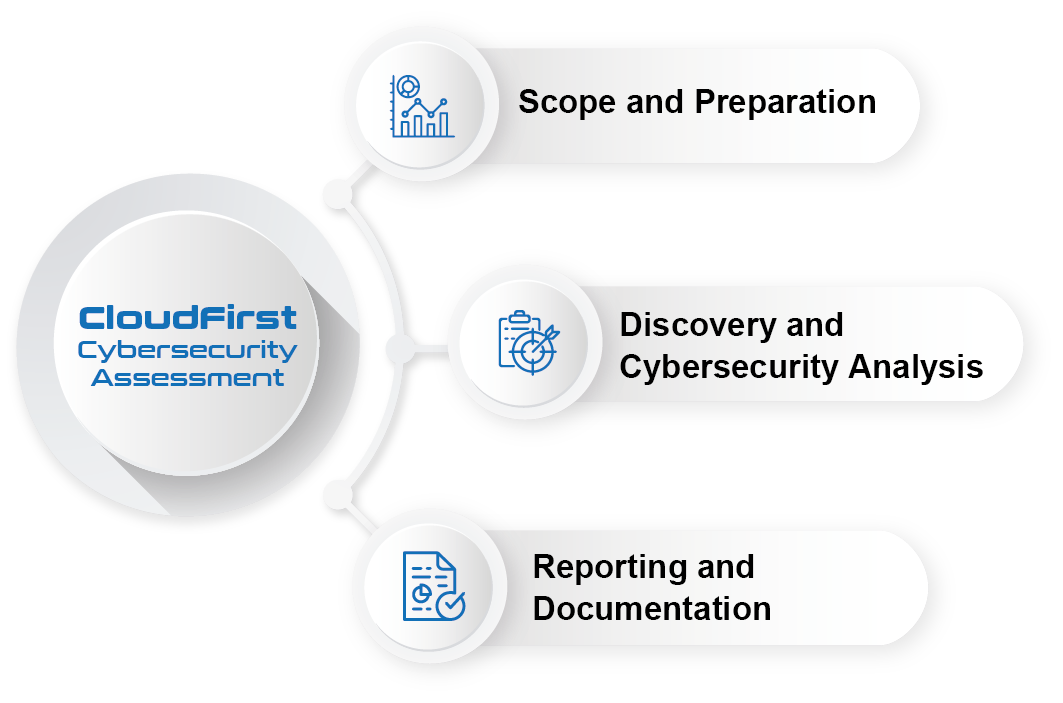
CloudFirst Assessment
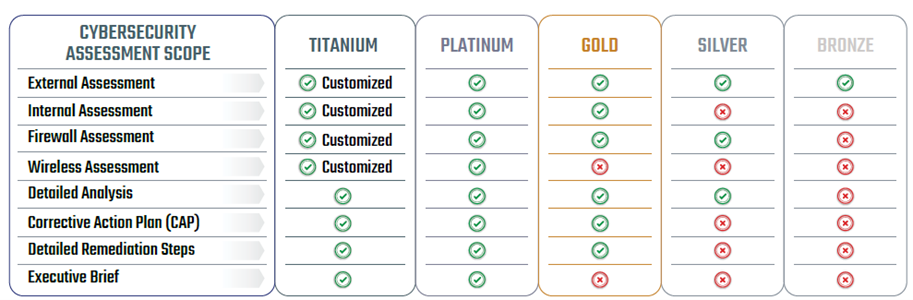
CIS Benchmark Assessment
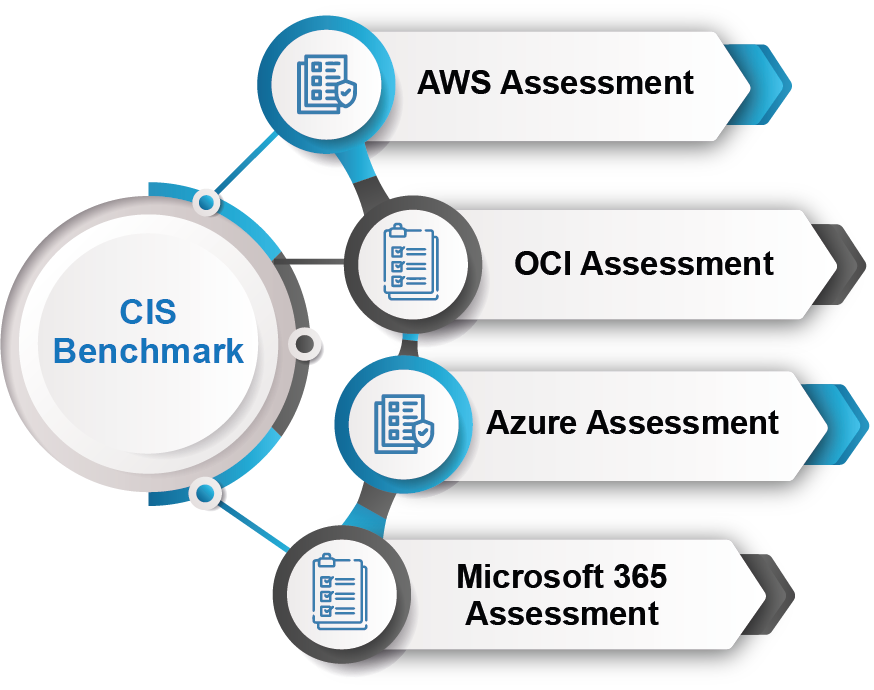
CIS AWS Assessment
- Secure AWS environment with CIS Benchmarks & Shared Responsibility Model.
- Covers AWS Foundations, Amazon Linux 2, and EKS.
- Provides prescriptive configuration best practices.
- Assess your organization’s cloud readiness and plan for effective adoption.
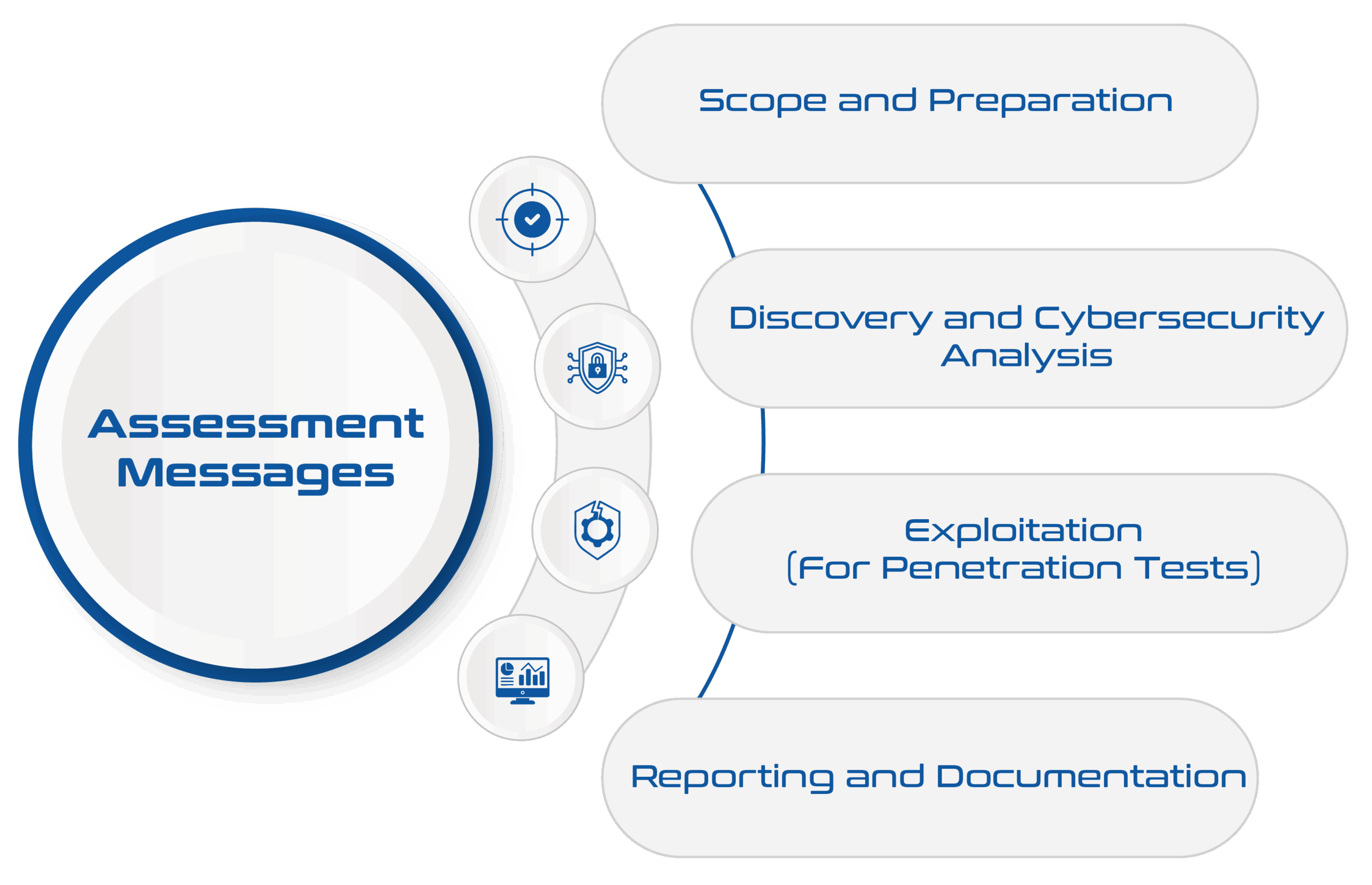
Phases
CIS OCI Assessment
- Enforce MFA for all console users.
- Restrict remote admin ports to within the enterprise network.
- Enable logging and notifications to detect anomalies and investigate incidents.
- CIS OCI Foundations Benchmark offers step-by-step secure configuration guidance for Identity, Networking, and Logging.
- Establishes a secure baseline configuration for OCI environments.
- Recommended for all OCI users to meet Level 1 CIS Benchmark compliance.
- Benchmark Report includes compliance status for each Level 1 control.
CIS Azure Assessment
- Links to CIS Azure Security Benchmark v2
- Advanced Data Security updated to Azure Defender
- New Azure Defender bundle recommendations
- Updated activity log alert remediation
- Deprecated feature recommendations removed
Evaluate readiness and cost for Azure migration:
- Azure Readiness: Suitability of servers for migration
- Monthly Cost Estimation: Compute & storage costs
- Monthly Storage Cost Estimation: Disk storage costs post-migration
CIS M365 Foundations Benchmark Assessment
- Establishes foundational security for Microsoft 365 adoption
- Not a complete list of all security configurations
- ecfirst reviews and reports compliance with CIS M365 secure baseline
- Focuses on Microsoft 365 infrastructure security