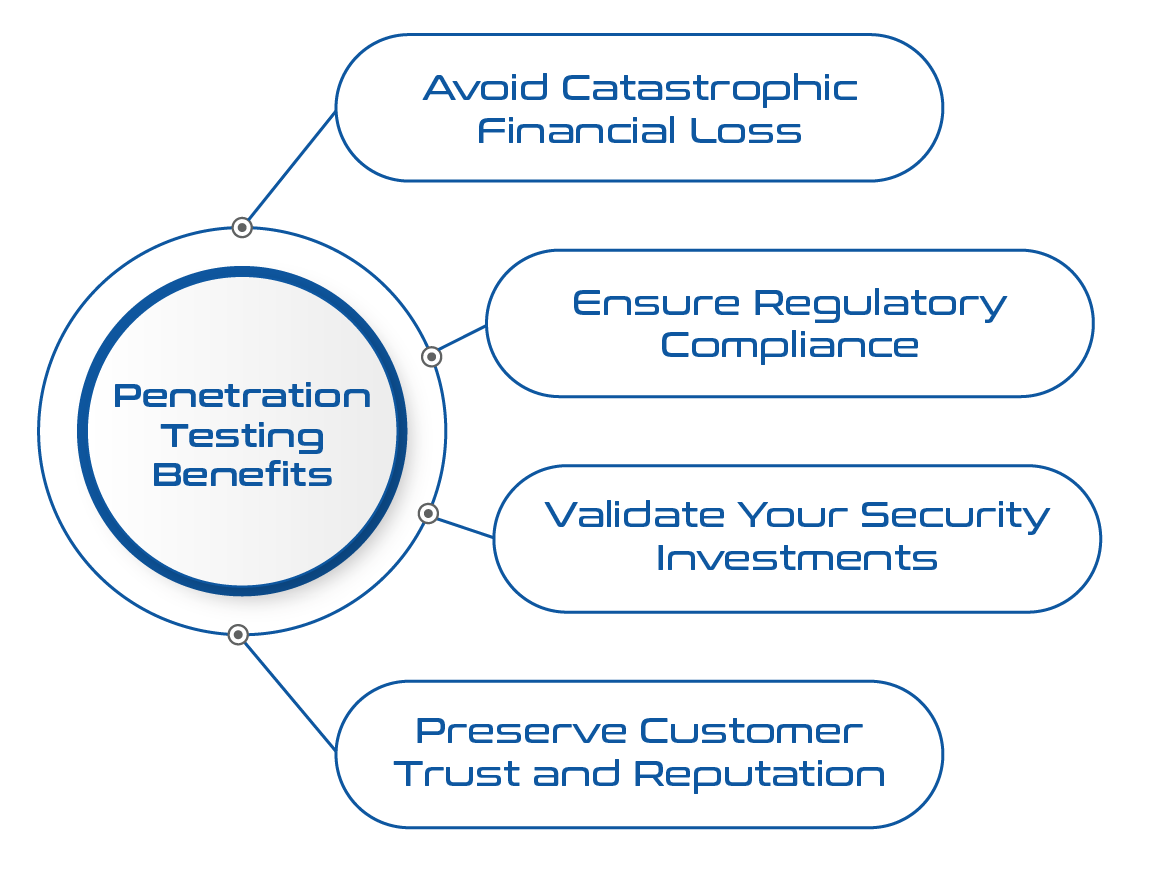
Objectives
Penetration Testing: Exposing Critical Security Gaps with Real-World Intrusions.
- Detect weak links with simulated attacks by experts
- Identify compliance gaps and internal/external security weaknesses
- Reveal likely attack paths and potential data compromises
- Assess vulnerabilities across systems to prioritize remediation
- Simulate real-world attacks to test external and internal access
- Highlight configuration, process, and staff practice weaknesses
External Pen Test
Simulates an attack from the public internet to breach your external, perimeter defenses.
Request a Proposal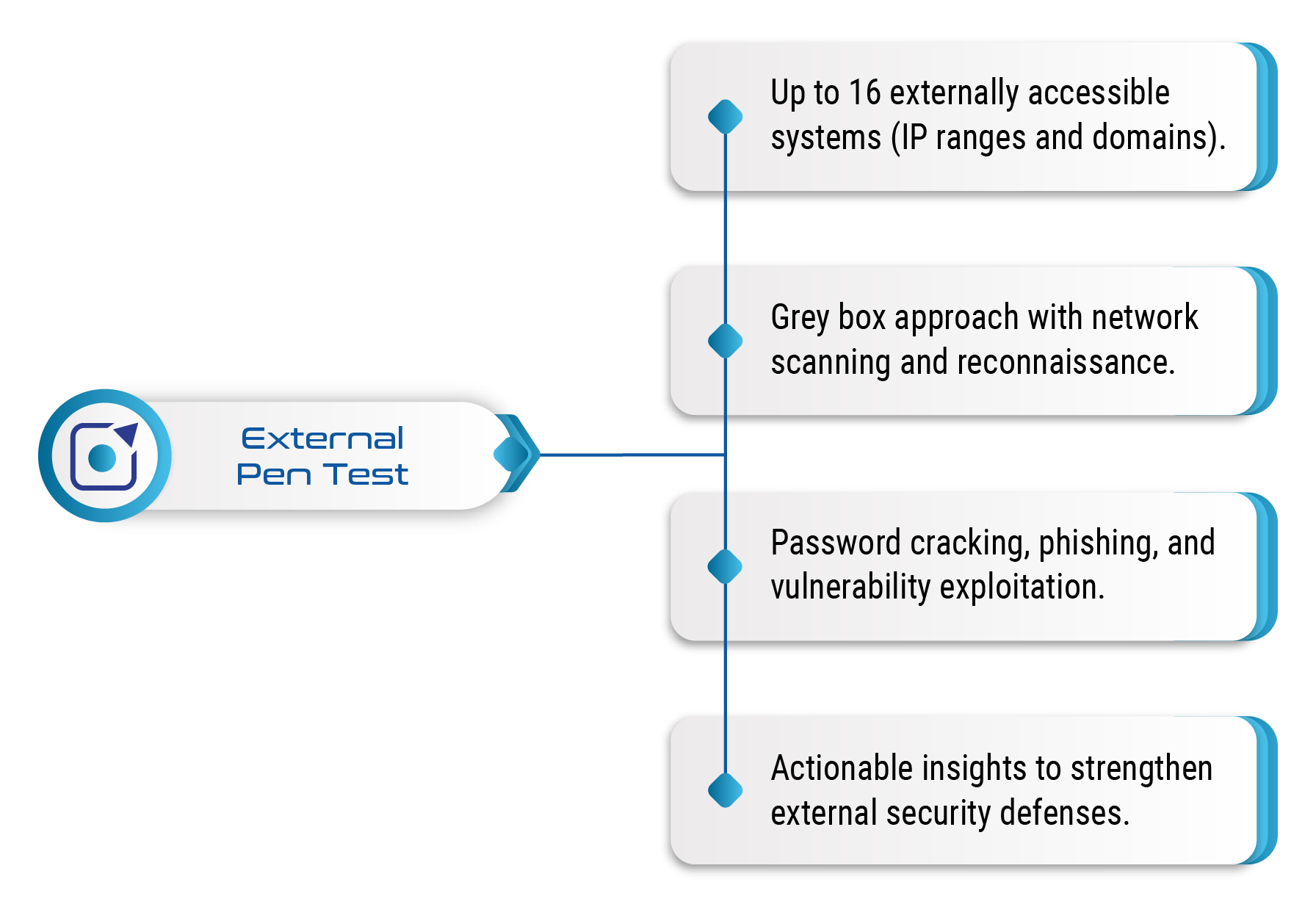
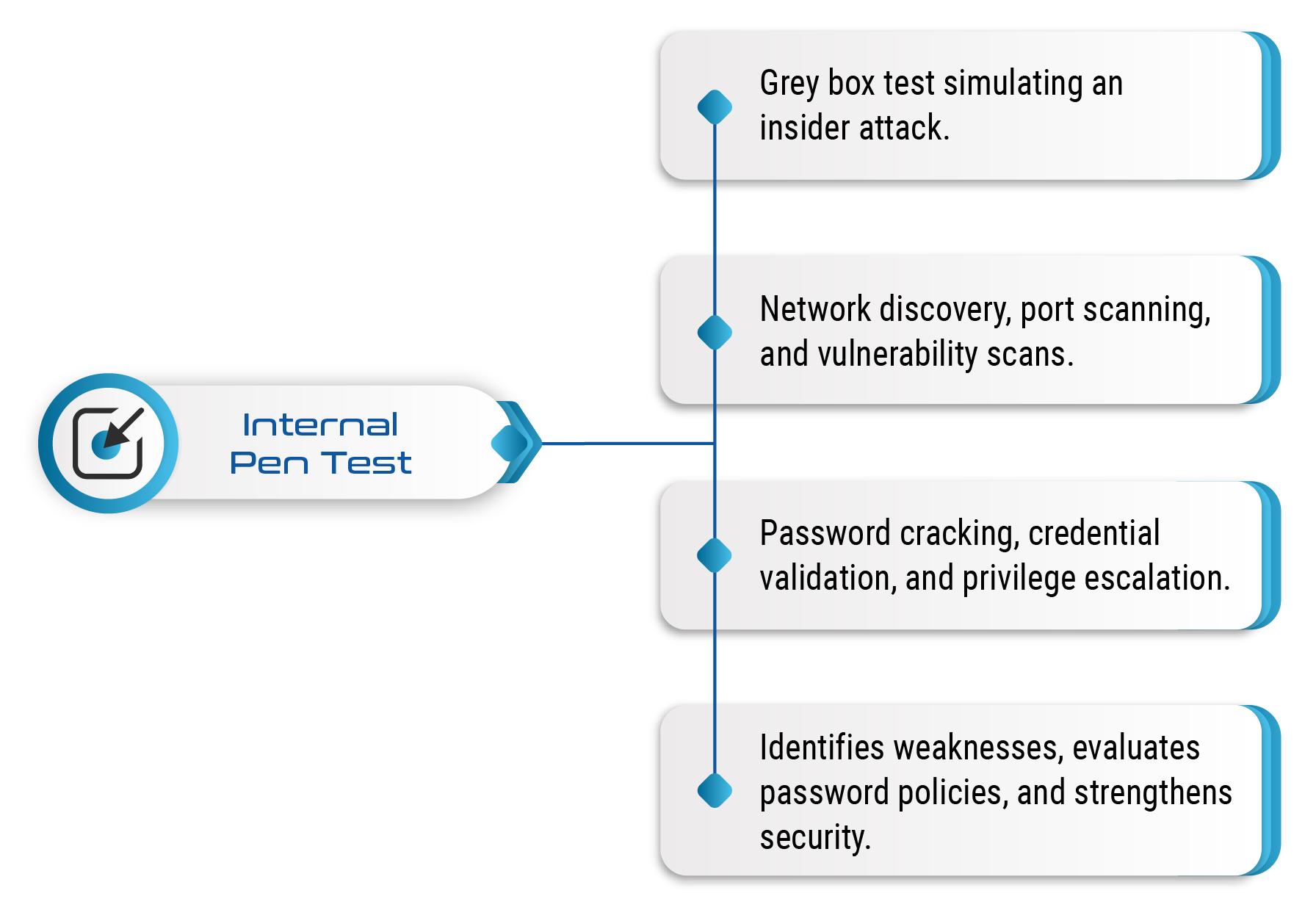
Internal Pen Test
Simulates an attack from an insider or a compromised user to test lateral movement and privilege escalation within your network.
Request a ProposalWeb Application Pen Test
Focuses on the application code, logic, and configuration to uncover flaws like SQLi and XSS that compromise user data.
Request a Proposal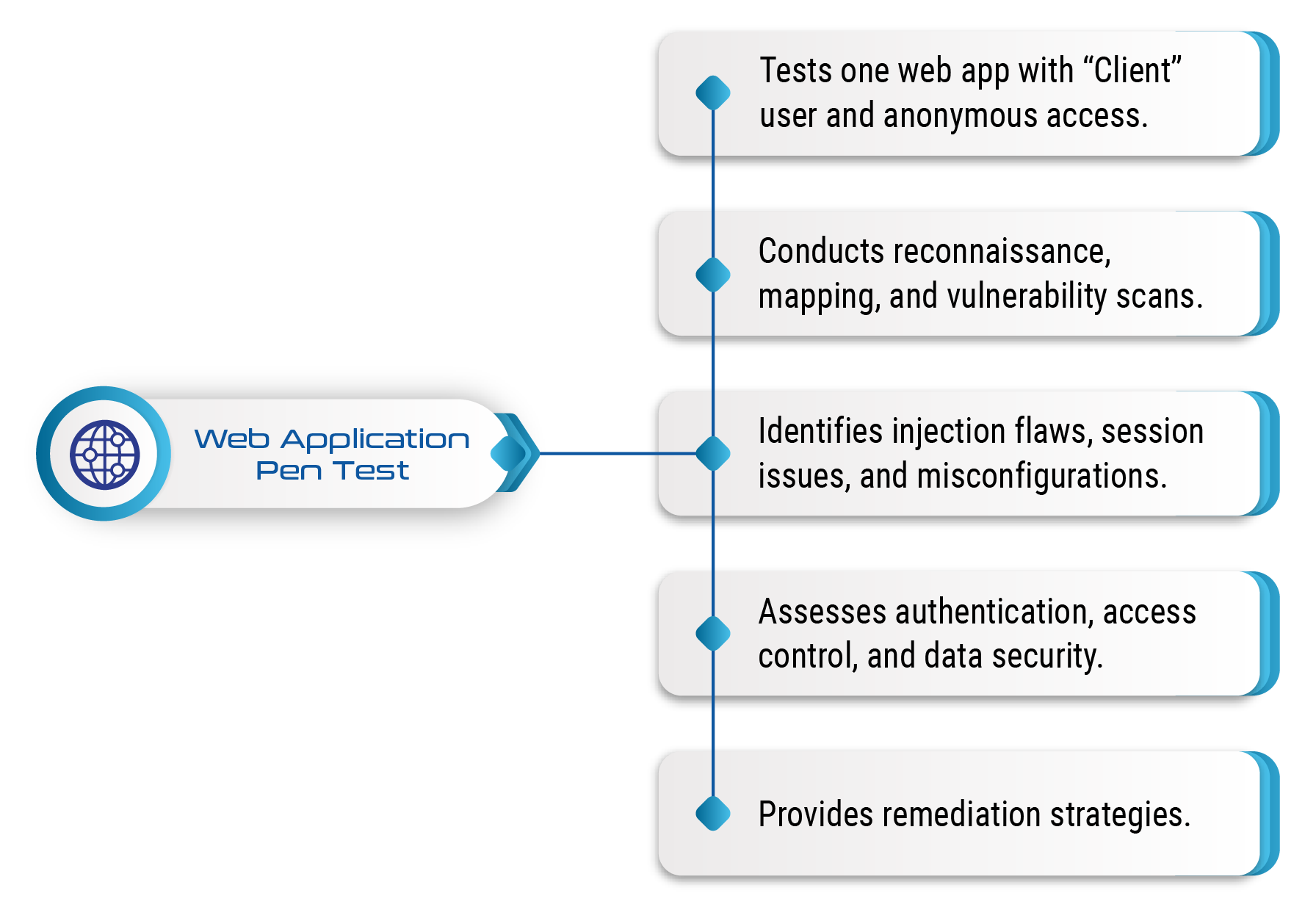
Penetration Test Methodology
- External Penetration Test
- Internal Penetration Test
- Web Application Penetration Test
- Web Application Cybersecurity Assessment
Reconnaissance
- Client personnel and cultural information
- Client business terminology
- Technical infrastructure information
- Cloud resource identification
- Continuous Integration/Continuous Development (CI/CD) third-party usage identification
Scanning
- Network discovery
- Network port and service identification
- Vulnerability identification
- Application/portal enumeration
Exploitation
- Password cracking
- Discovered credential usage
- Manual and automated vulnerability validation
- Privilege escalation
- Additional tool installation
- Data discovery
Scanning
- Network discovery
- Network port and service identification
- Vulnerability identification
- Enumeration
Exploitation
- Password cracking
- Discovered credential usage
- Manual and automated vulnerability validation
- Privilege escalation
- Additional tool installation
- Data discovery
Reconnaissance
- Client personnel and cultural information
- Client business terminology
- Technical infrastructure information
Mapping
- Network Discovery
- Network Port and Service Identification
- Analyzing HTTPS Support
- Identify Virtual Hosting and Load Balancers
- Analyze Software Configuration
- Spider the site/application
- Application flow charting
- Relationship analysis
- Session analysis
Discovery
- Automated Vulnerability Scanning
- Information Leakage & Directory Browsing Discovery
- Username Harvesting & Password Guessing
- Command Injection Discovery
- Directory Traversal & File Inclusion Discovery
- SQL Injection Discovery
- Cross-site Scripting (XSS) Discovery
- Cross-site Request Forgery (CSRF) Discovery
- Session Flaw Discovery
- Insecure Redirects & Forwards Discovery
Exploitation
- Exploit identified Enumeration flaws
- Exploit identified Bypass flaws
- Exploit identified Injection flaws
- Exploit identified Session flaws
- Chain exploits together, pivot to other systems, data exfiltration, raid the fridge, etc.
Mapping
- Analyzing HTTPS Support
- Analyze Software Configuration
- Crawl the site/application
- Relationship analysis
- Session analysis
Discovery
- Automated Vulnerability Scanning
- Broken Access Controls
- Cryptographic Failures
- Injection
- Insecure Design
- Security Misconfiguration
- Vulnerable and Outdated Components
- Identification and Authentication Failures
- Software and Data Integrity Failures
- Security Logging and Monitoring Failures
- Server-side Request Forgery


